Product Advantages
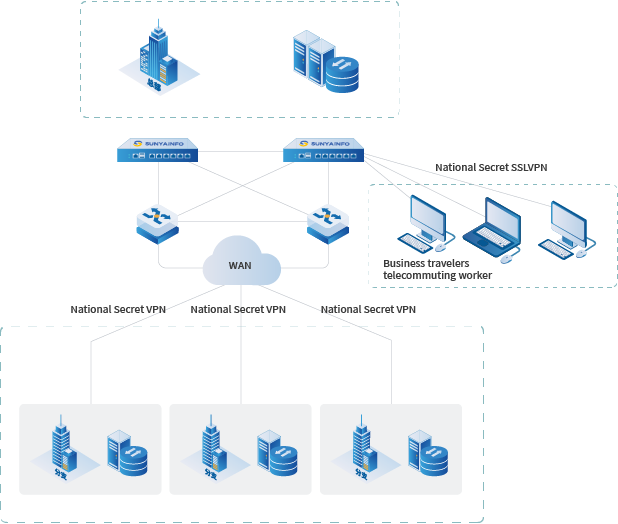
Complies with the technical specifications of the National Security Bureau
The product is developed strictly in accordance with the SSL VPN Technical Specification and IPSec VPN Technical Specification formulated by the National Cryptography Administration, and supports the SM1, SM2, SM3, and SM4 commercial password algorithms specified by the National Cryptography Administration. It has passed the testing of the National Cryptography Administration's Commercial Password Testing Center.
Rich authentication methods
Supports multiple identity authentication methods, including local authentication, SMS authentication, WeChat authentication, digital certificate authentication, dynamic password authentication, hardware signature authentication, Portal authentication, and third-party authentication (LDAP, Radius, etc.), and can combine multiple authentication methods.
High performance transmission acceleration
We independently developed the secure operating system SunyaOS, which combines hardware based high-speed streaming and business based intelligent scheduling to achieve ultra high speed collection and forwarding of data packets. Multi core polling parallel processing greatly improves the encryption and decryption performance of the system. Using hardware password cards that comply with the requirements of the national password regulatory authority for encryption and decryption operations, meeting the security technical requirements of the password module.
Multi platform compatibility
It can provide terminals for Windows, Android, MAC, IOS and other platforms, and fully support access authentication and control for domestic operating system terminal environments such as Galaxy Kirin.
Refined application control
Supporting precise application recognition of over 5000, based on three application recognition technologies: DPI, DFI, and intelligent behavior analysis, it can accurately perform fine-grained access control based on applications.
Support fine-grained control of internal network resources by all access users, which can not only control the access permissions of resources, but also limit the time limit of resource access.
Intelligent and efficient operation and maintenance management
Support integrated management of network connectivity and security policies, support intelligent policy analysis, able to detect redundant policies, hidden policies, conflict policies, combinable policies, null policies, expired policies, etc., and provide policy optimization suggestions to simplify daily operation and maintenance management.
In conjunction with the SD-WAN platform, it supports multi branch interconnection, customizable Overlay network models such as Hub Spark and Full Mesh, and solves the dilemma of large-scale deployment and management, achieving zero configuration deployment of devices and a minute level start.
User Value
01
Reliable national security access solution
Provide users with data encryption transmission solutions based on national encryption algorithms and national encryption negotiation modes, ensuring the security of branch and headquarters, remote user access, and meeting the requirements of level protection compliance.
02
Rich authentication methods
Provide users with multiple identity authentication methods that can be combined according to different usage scenarios and needs, strengthen user identity auditing, and enhance the security of user access.
03
Simple and easy-to-use management
Combined with the SD-WAN platform, centralized management of VPN security gateways can be achieved, enabling zero device configuration and minute level deployment, providing multiple networking models for branch interconnection, and reducing operation and maintenance costs.
04
High reliability deployment
Provide multiple reliability technologies to protect the security and reliability of user networking from dimensions such as device reliability and link reliability.
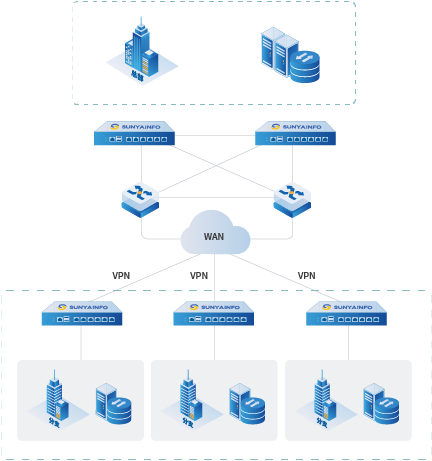
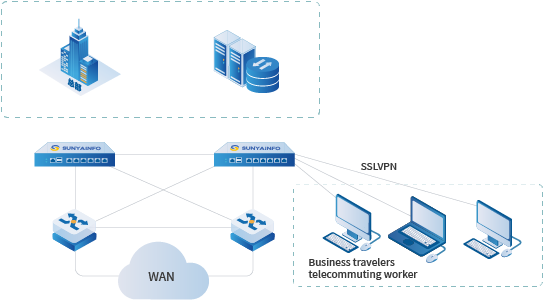
Application Scenarios