Product Advantages
High performance processing architecture
Sunyainfo next-generation firewall independently developed the secure operating system SunyaOS, which combines hardware based high-speed streaming and business based intelligent scheduling to achieve ultra-high-speed collection and forwarding of data packets. The software architecture adopts a separation of control and transmission, and the zero-copy technology of kernel bypass maximizes the security processing performance.
Adapting to Cloud based Firewalls
The next-generation firewall of Sunyainfo supports virtualization deployment and runs on mainstream virtualization platforms such as VMware, KVM, and Hyper-V. It is compatible with Alibaba Cloud, Tencent Cloud, Huawei Cloud, Jinshan Cloud, Tianyi Cloud, Mobile Cloud, Unicom Cloud, Ziguang Cloud, Qingyun, etc., providing professional boundary security protection for cloud networks and cloud services.
Powerful network capabilities
It has multiple static, dynamic, and policy routes, rich NAT functions, and provides various VPNs such as IPSec, SSL, GRE, VXLAN, L2TP, etc. It has comprehensive support for IPv4 and IPv6 dual stack networks, and supports comprehensive deep security protection based on IPv6, meeting the requirements of complex network applicability.
Digital Asset Security Management
The next-generation firewall of Sunyainfo supports one click asset discovery, utilizing various methods such as traffic learning, scanning and detection, terminal linkage, and manual input to quickly discover and manage digital assets. Conduct a unified asset security review based on attributes such as department, business system, and importance.
Multidimensional detection and defense
The integrated security engine provides protection capabilities such as application recognition, application auditing, intrusion prevention, virus protection, URL classification, and web content filtering. Combined with cloud-based TIP intelligence capabilities, it establishes defense capabilities for hot attack events in a timely manner.
A fully open API that can collaborate and integrate with existing security systems, supporting linkage solutions with situational awareness, sandboxes, NTA, and other products to jointly build a three-dimensional defense system.
Intelligent and efficient operation and maintenance management
Support intelligent policy analysis, able to detect redundant policies, hidden policies, conflicting policies, combinable policies, empty policies, expired policies, etc., and provide policy optimization suggestions to simplify daily operation and maintenance management.
Cooperate with the centralized management platform to solve the dilemma of large-scale deployment and management, support remote batch upgrades of system versions and feature libraries, provide real-time monitoring of firewall status, security situation analysis, configuration distribution and backup, centralized log management, etc.
User Value
01
Efficient and Reliable - Ultimate Business Experience
Based on our self-developed high-speed diversion and intelligent scheduling engine, we achieve ultra-high-speed collection and forwarding of data packets. Through a software architecture that separates transfer and control, we use zero copy technology with kernel bypass to ensure that devices can maintain high performance in high traffic and complex scenarios while still running stably and reliably.
02
Intelligent Defense - Comprehensive Network Attack Protection
A comprehensive security defense system has been formed through pre risk monitoring, in-process protection response, and post evidence analysis, providing users with security capabilities such as application identification and auditing, intrusion prevention, virus protection, URL classification, web content filtering, and multiple DOS/DDOS attack protection. It supports linkage with external security systems such as intelligence, EDR, NDR, and sandboxes, enhancing the security protection capabilities of devices.
03
Minimalist operation and maintenance - intelligent and efficient operation and maintenance management
Intelligent analysis with strategies, simplifying the daily operation and maintenance management of administrators, with multi-dimensional visual statistical analysis functions around users, applications, security, etc., intuitively presenting the network status of users, and facilitating post traceability and positioning.
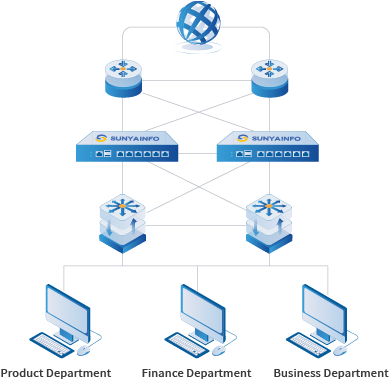
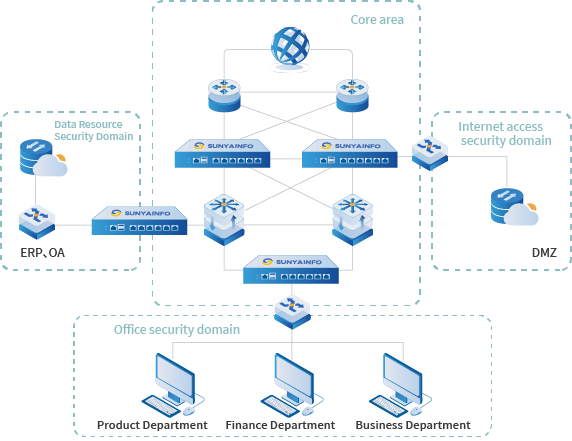
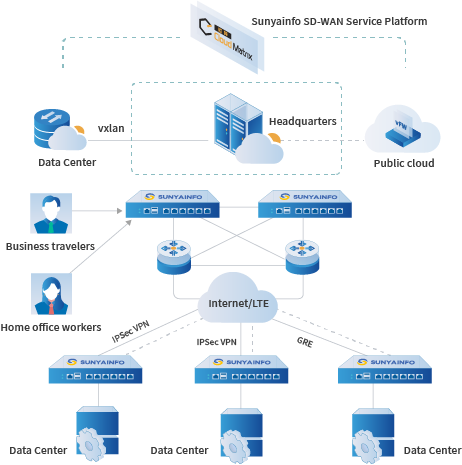
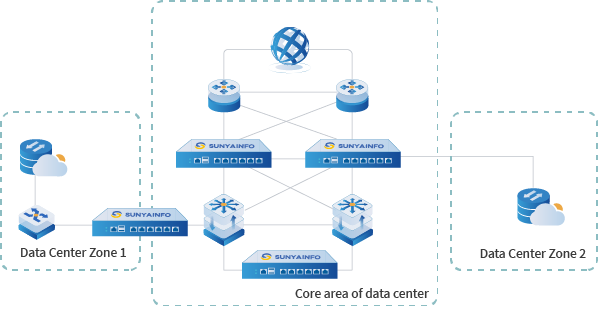
Application Scenarios