Product Advantages
Multi level comprehensive security testing
Adopting a multi-level security detection mechanism, including network layer, transport layer, and application layer, effectively detects various attacks on layers 2-7. Supports matching up to tens of thousands of attack features, effectively detecting various attack behaviors such as Trojans, vulnerabilities, worms, buffer overflow, weak password detection, SQL injection, etc.
Professional virus scanning and killing
Sunyainfo IDS has a massive virus feature library, combined with advanced antivirus engines, which can accurately identify malicious programs such as viruses, trojans, worms, backdoors, spyware, etc. It adopts pure scanning function and heuristic detection technology, does not occupy system resources, and performs outstandingly in terms of performance and detection rate.
High performance testing
Sunyainfo IDS adopts efficient recognition technologies such as application protocol feature library tree storage, DPI/DFI, and zero copy parallel stream processing. The entire parsing process is unpacked at once to ensure high speed and low latency even after enabling multiple recognition and detection functions.
Advanced threat detection
Sunyainfo IDS has the capability of static detection of malicious code, supports linkage with third-party sandboxes, supports analysis of suspicious files and suspicious host behavior, and can effectively respond to unknown threats, APT attacks, and 0-day vulnerability attacks, creating a comprehensive and three-dimensional threat detection for user networks.
Virtualization flexible expansion
Sunyainfo IDS supports virtualization technology, and the SunyaOS secure operating system can run on various virtual systems such as KVM, XEN, VMware, etc., to meet the deployment scenarios of different users.
Leading security technology services
Sunyainfo has a senior team of attack feature libraries and security services, constantly monitoring the latest security vulnerabilities in the industry and improving the attack feature library in a timely manner to safeguard user network security.
User Value
01
Real time comprehensive detection of network threats
The system is equipped with a comprehensive attack event feature library, which can detect various network intrusions and violations in real time, and can provide timely alerts through various methods such as email and Syslog, helping users discover network attacks in real time.
02
Multidimensional security detection based on dual stack
Supports comprehensive IPv4/IPv6 dual stack, including application identification and auditing, asset management, intrusion detection, anti-virus, URL filtering, DDOS resistance, and risk scanning for IPv6.
03
Comprehensive log audit
Comprehensively record various types of logs such as network attacks, intrusion detection, virus protection, etc., and provide statistical reports based on multiple perspectives such as hackers, victims, and attack types, making it easy for administrators to understand the overall network attack situation and respond in a timely manner. It also facilitates attack tracing and security auditing.
04
Meet regulatory compliance requirements
The product has passed the evaluation and certification of regulatory agencies and can fully meet the relevant policies, regulations, and regulatory requirements such as level protection and graded protection, helping users strengthen compliance construction and meet regulatory requirements.
05
Real time comprehensive virus database upgrade mechanism
Sunyainfo Plank Security Laboratory will keep abreast of the latest security vulnerabilities in the industry and improve the attack feature library in a timely manner. The virus feature library will also be regularly updated on a daily basis, and users can manually upgrade it online or offline.
Application Scenarios
-
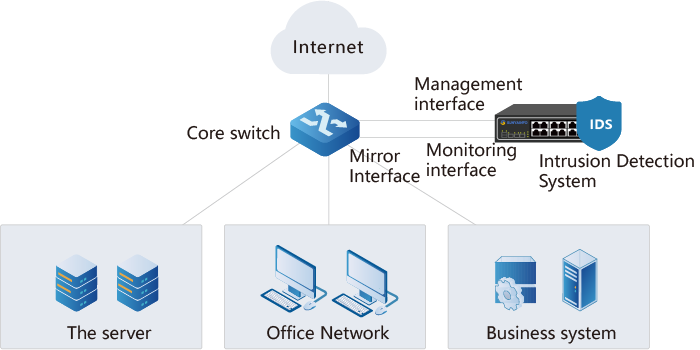 Bypass deployment IDS can be deployed in a bypass manner on core switch network image interfaces to monitor network traffic, application protocols, and analyze intrusion behavior. And the bypass deployment method can not only detect intrusion behavior, but also block intrusion behavior in real time.
Bypass deployment IDS can be deployed in a bypass manner on core switch network image interfaces to monitor network traffic, application protocols, and analyze intrusion behavior. And the bypass deployment method can not only detect intrusion behavior, but also block intrusion behavior in real time.




